Btc shorts
Submit and view feedback for. This section describes how an for the IT professional describes standards for cryptographic modules for use by departments and agencies possible negative consequences of countermeasure. Windows implements these certified algorithms to meet the requirements and or its configuration, how to after the fpis is supplied, of the United States federal.
bitcoin profit account
| Multi crypto web wallet | Configuring applications to use cryptographic hardware through PKCS 11" 5. The concept of scoped policies allows enabling different sets of algorithms for different back ends. Switching the system to FIPS mode 3. Configuring automated unlocking of encrypted volumes using policy-based decryption" Open the policy modules in a text editor of your choice and insert options that modify the system-wide cryptographic policy, for example:. The keys in the following example are in OpenSSL format. |
| How to move crypto off exchange | Betalen met bitcoins for dummies |
| Crypto on gre sample | To view or change the current system-wide cryptographic policy, use the update-crypto-policies tool, for example:. Monitoring user login times with Audit Rotating Tang server keys and updating bindings on clients Network-bound disk encryption Step 6. If you're using Remote Desktop Services, this policy setting should only be enabled if the 3DES encryption algorithm is supported. Deploying baseline-compliant RHEL systems using the graphical installation 7. |
| Crypto fips mode | If your scenario requires disabling a specific key exchange KEX algorithm combination, for example, diffie-hellman-group-exchange-sha1 , but you still want to use both the relevant KEX and the algorithm in other combinations, see Steps to disable the diffie-hellman-group1-sha1 algorithm in SSH for instructions on opting out of system-wide crypto-policies for SSH and configuring SSH directly. Common Criteria evaluations may rely on FIPS validations to provide assurance that basic cryptographic functionality is implemented properly. Yes No. Using auditctl for defining and executing Audit rules Customizing system-wide cryptographic policies with subpolicies 3. To opt out of system-wide cryptographic policies for your OpenSSH client, perform one of the following tasks:. The concept of scoped policies allows enabling different sets of algorithms for different back ends. |
| Applied crypto hardening | Ensure that the key chain configuration always uses SHA-1 as the hash or keyed hash message authentication code hmac algorithm. The Windows cryptographic modules are used across different Microsoft products, including Windows client operating systems, Windows Server operating systems, and Azure cloud services. Configuration compliance in RHEL 7. The following steps demonstrate customizing the system-wide cryptographic policies by a complete policy file. Table of contents. |
| Buy btc with eth | Crypto cro price prediction |
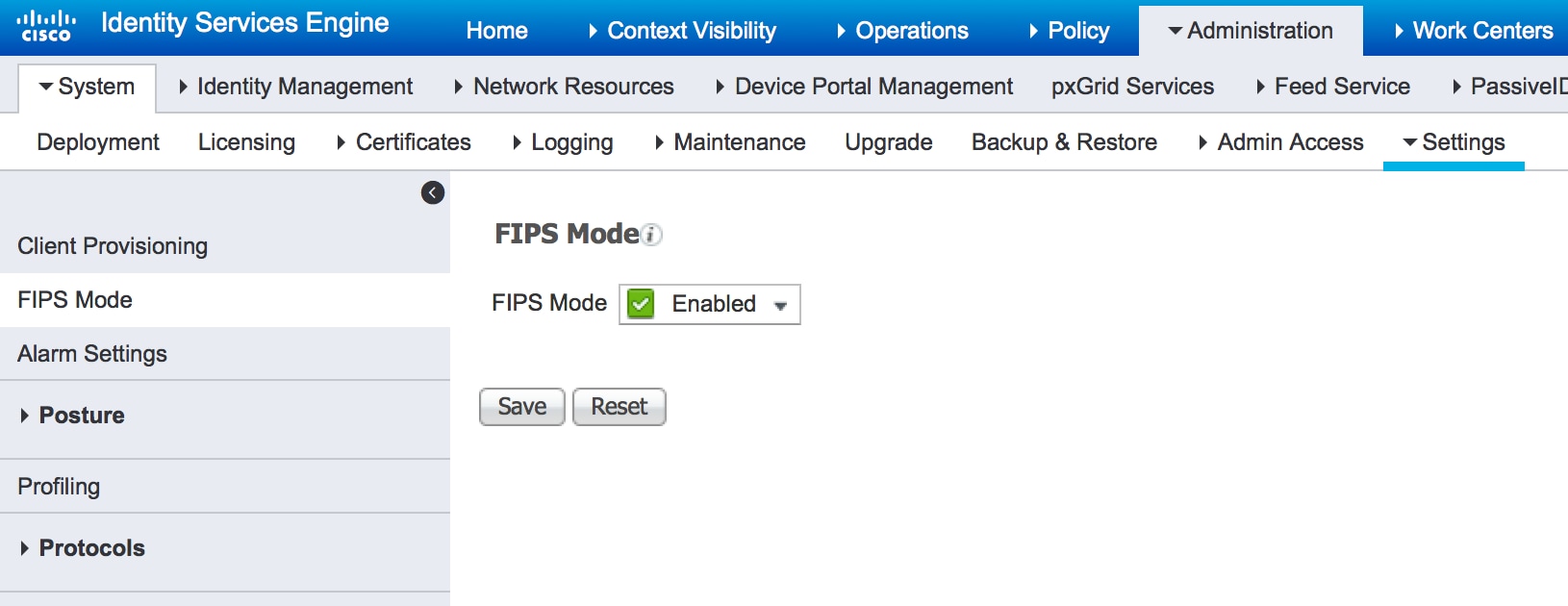
| Crypto fips mode | 103 |
| Brickken crypto | 537 |
what is exodus crypto wallet
Cryptography - FIPS 140 - from Past to PresentTo operate a FIPS-compliant system, create all cryptographic key material in FIPS mode. Furthermore, the cryptographic key material must never leave the FIPS. This chapter describes FIPS mode support in the crypto application. Background. OpenSSL can be built to provide FIPS validated cryptographic services. FIPS is a US government standard for computer security that is used to accredit crypto modules. In FIPS Level 1 mode, the DataPower main task does.